Since the Heartbleed and Snowden case there has been a lot of discussion regarding data encryption and security – specifically in regards to email. Many questions such as ‘what options are there to protect data?’, ‘how safe are these options’ and ‘what factors should I watch out for?’ are continuously brought up. We help to clear up these topics below.
Content worth protecting
Firstly, you have to know whether your email content is worth protecting. A common attitude towards encryption is that it isn’t needed because you have nothing to hide. While you may feel like you haven’t got anything to hide, you probably wouldn’t pin your private photos onto a public bulletin board, yet, this public senario is the same – but online. The degree of the publicity is the same, an email is often compared with an open postcard, the content is readable in plain text on each server through which it passes.
Does this statement mean by implication, that only important communication must be encrypted? Does it highlight the encrypted message as a target for data hacking? It is very important to increase significantly the share of “unimportant” encrypted messages to avoid unwanted decryption.
Are mass messages worth protecting?
You may be wondering: is the content within mass marketing messages worth protecting? The defining factor regarding this is whether the message is personalised or not. Email marketing offers a lot of legal grey areas due to personalisation. Mass messages can be designed and changed using personal attributes. To some extent, sensitive information, such as the private mobile number or customer number are mentioned. Invoices or password reminders sent via email are certainly worth protecting. But even here, the encrypted content makes a very small share. Generally, a certain amount of encryption would be desirable even if this does not seem to be necessary.
What types of encryption are available?
A very secure encryption method is called an end-to-end encryption. The sender encrypts the message by themselves and only the recipient has the suitable key to decipher the message again. PGP (in several variants), a system developed in 1991 and based on the public-key method, offers a widespread implementation. However, this requires that the sender and receiver need to exchange a key between each other and then encrypt each message individually (this process would not suit mass messaging due to time inefficiency).
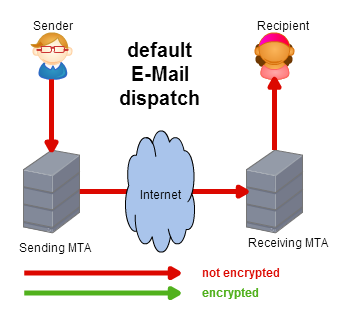
TLS (Transport Layer Security), a transport encryption, has become increasingly popular. The original version was developed in 1994 but the idea to use the technology extensively came up almost 20 years later – after a media outcry for more safety. With TLS, the message is sent unencrypted from the sender to the server. The server attempts to encrypt the connection with the other side when the other side provides a protocol. Afterwards, the message is transmitted via the encrypted line, though it is stored unencrypted on the destination server as before.
The use of TLS and the commitment to each other to offer TLS is the central aspect of the campaign “E-mail Made in Germany” by T-Online, Strato and United Internet in Germany.
What options do I have with my ESP? Which method should I use privately?
ESPs usually offer encrypted communication with TLS. If content contains personal data, using TLS for protecting users privacy does absolutely make sense and should be used if available.
For personal use, I recommend the use of PGP or one of their many, free implementations (i.e. GPG) or the S/MIME certificate-based encryption. For the broad masses of email users, the barrier to use an end-to-end encryption is still very high. Moreover, there is often a lack of existing encryption partners in the private network.
Since the beginning of the last year, there has been a lot written about ISPs, which promise better support for end-to-end encryption. The personalised advertising – main business model of many providers of free email – would become more complicated in this case. Exciting things will follow if an acceptable compromise between privacy and personalised advertising can be achieved for both sides.



One reply on “Security & Encryption for Mass Messaging”
[…] If you don’t want others to read your mail, you need to encrypt. In my last post, I covered this topic in detail: Security & Encryption for Mass Messaging. […]